考点: 冰蝎流量解密+部分明文攻击
看请求路由可以知道 shell.php是上传的马子
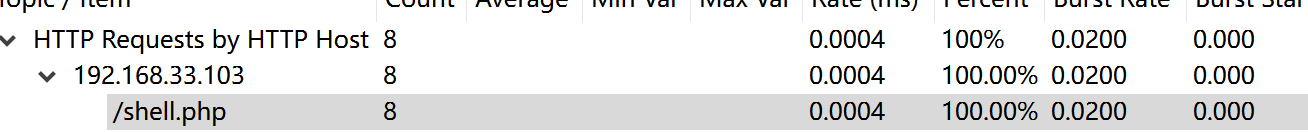 过滤器
过滤器 http
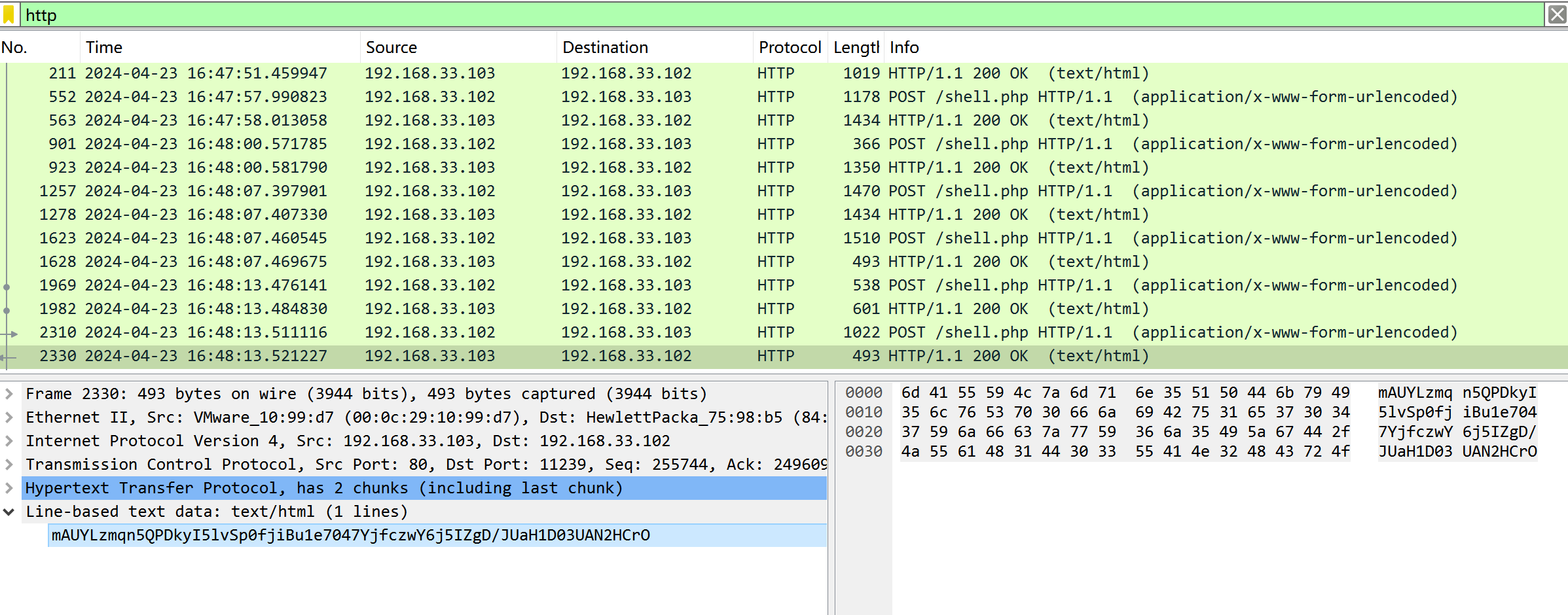 加密返回包+前16为完整base编码字符 一眼冰蝎流量解密
爆破aes常用密码 就是冰蝎默认aes密码
加密返回包+前16为完整base编码字符 一眼冰蝎流量解密
爆破aes常用密码 就是冰蝎默认aes密码 e45e329feb5d925b
冰蝎从开头流量都是连接初始化之类的,==一般关键数据在后面==
从后向前看发现 对通信流量解密并且处理后
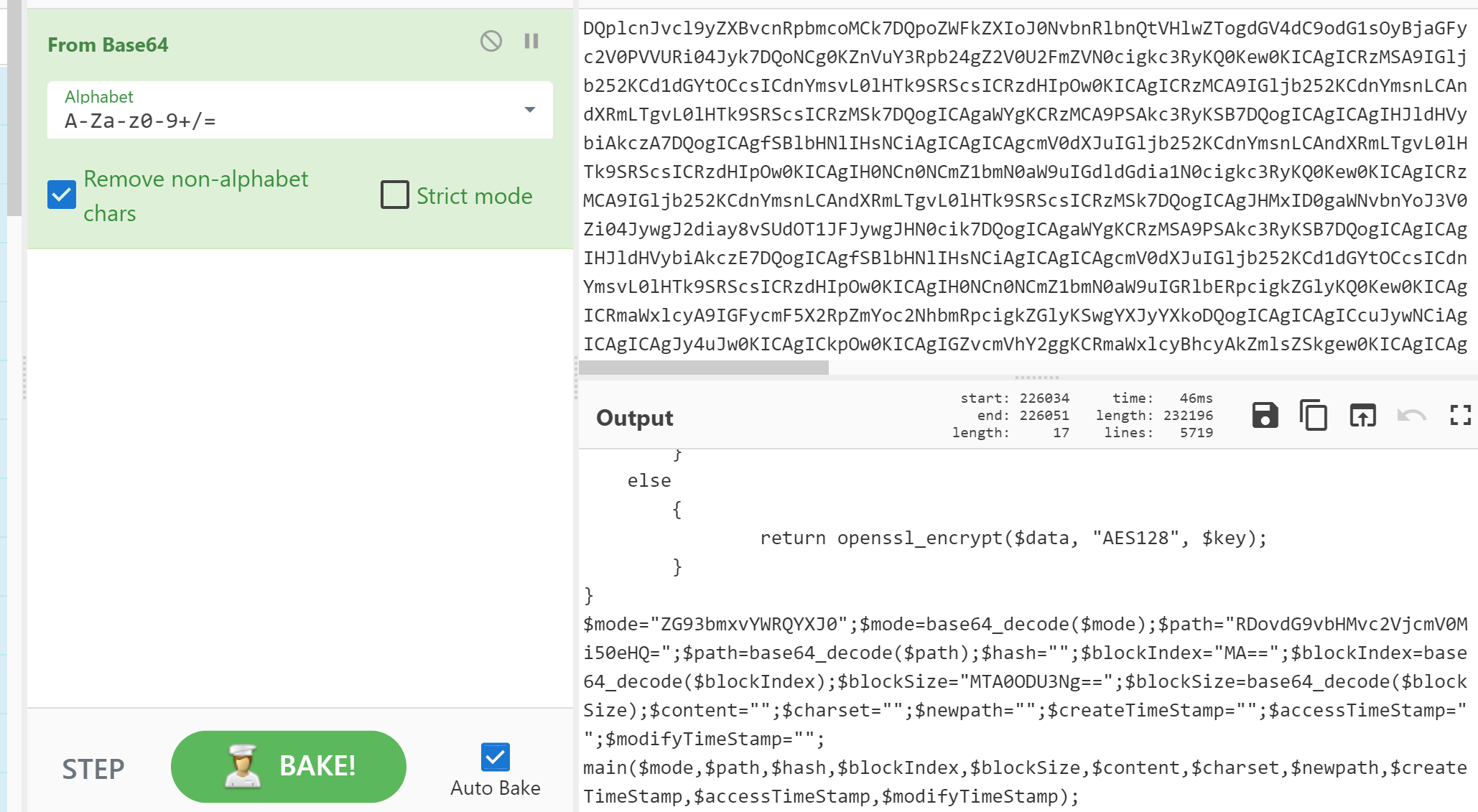 No.1962 request请求数据解密 关键数据
No.1962 request请求数据解密 关键数据
$mode="downloadPart";$mode=base64_decode($mode);$path="D:/tools/secret2.txt";$path=base64_decode($path);$hash="";$blockIndex="0";$blockIndex=base64_decode($blockIndex);$blockSize="MTA0ODU3Ng==";$blockSize=base64_decode($blockSize);$content="";$charset="";$newpath="";$createTimeStamp="";$accessTimeStamp="";$modifyTimeStamp="";
main($mode,$path,$hash,$blockIndex,$blockSize,$content,$charset,$newpath,$createTimeStamp,$accessTimeStamp,$modifyTimeStamp);
模式: downloadPart 路径 :D:/tools/secret2.txt 存在文件 secret2.txt
对应响应包
No.1982 {"msg":"Hello, but what you're looking for isn't me.","status":"success"}
接着向上解密流量
No.1623
$mode="check";$mode=base64_decode($mode);$path="D:/tools/temp.zip";$path=base64_decode($path);$hash="a81d4f6bbcd72366";$hash=base64_decode($hash);$blockIndex="";$blockSize="";$content="";$charset="";$newpath="";$createTimeStamp="";$accessTimeStamp="";$modifyTimeStamp="";
main($mode,$path,$hash,$blockIndex,$blockSize,$content,$charset,$newpath,$createTimeStamp,$accessTimeStamp,$modifyTimeStamp);
No.1628
{"status":"success","msg":"ok"}
关键信息$mode=“check” $path=“D:/tools/temp.zip” 存在文件 temp.zip
感觉操作是获取了服务器上的文件信息
先check —>downloadPart(返回包存在数据信息)
那上一个 downloadPart就有temp.zip文本数据
N0.1278
{"msg":"VUVzREJCUUFBUUFBQUc1MWwxaDR1a0pLTmdBQUFDb0FBQUFMQUFBQWMyVmpjbVYwTVM1MGVIUnRnbEhFV1BEU3lEVDZwQm9YanBmZEdldlhkMU52WjlDbkxHNFVuN3k4MytMU0wyS09CWDBwcUZ0dFJnaTJHcEdWZDZxVWI1cFFTd01FRkFBQkFBQUE3bldYV0pEZnZFczRBQUFBTEFBQUFBc0FBQUJ6WldOeVpYUXlMblI0ZE9WUS9NZDhpWDNDajgxN0dqVERicGI1MThNNkNTUTFvQ0ZCR2RscCtMY1ltNTNNaVFKdnZlclB1SEIxZis3RFF5cmNwWDNGbDhUcFVFc0JBajhBRkFBQkFBQUFibldYV0hpNlFrbzJBQUFBS2dBQUFBc0FKQUFBQUFBQUFBQWdBQUFBQUFBQUFITmxZM0psZERFdWRIaDBDZ0FnQUFBQUFBQUJBQmdBVE9DdmkwbVYyZ0VBQUFBQUFBQUFBQUFBQUFBQUFBQUFVRXNCQWo4QUZBQUJBQUFBN25XWFdKRGZ2RXM0QUFBQUxBQUFBQXNBSkFBQUFBQUFBQUFnQUFBQVh3QUFBSE5sWTNKbGRESXVkSGgwQ2dBZ0FBQUFBQUFCQUJnQTU0MEdHMHFWMmdFQUFBQUFBQUFBQUFBQUFBQUFBQUFBVUVzRkJnQUFBQUFDQUFJQXVnQUFBTUFBQUFBQUFBPT0=","status":"c3VjY2Vzcw=="}
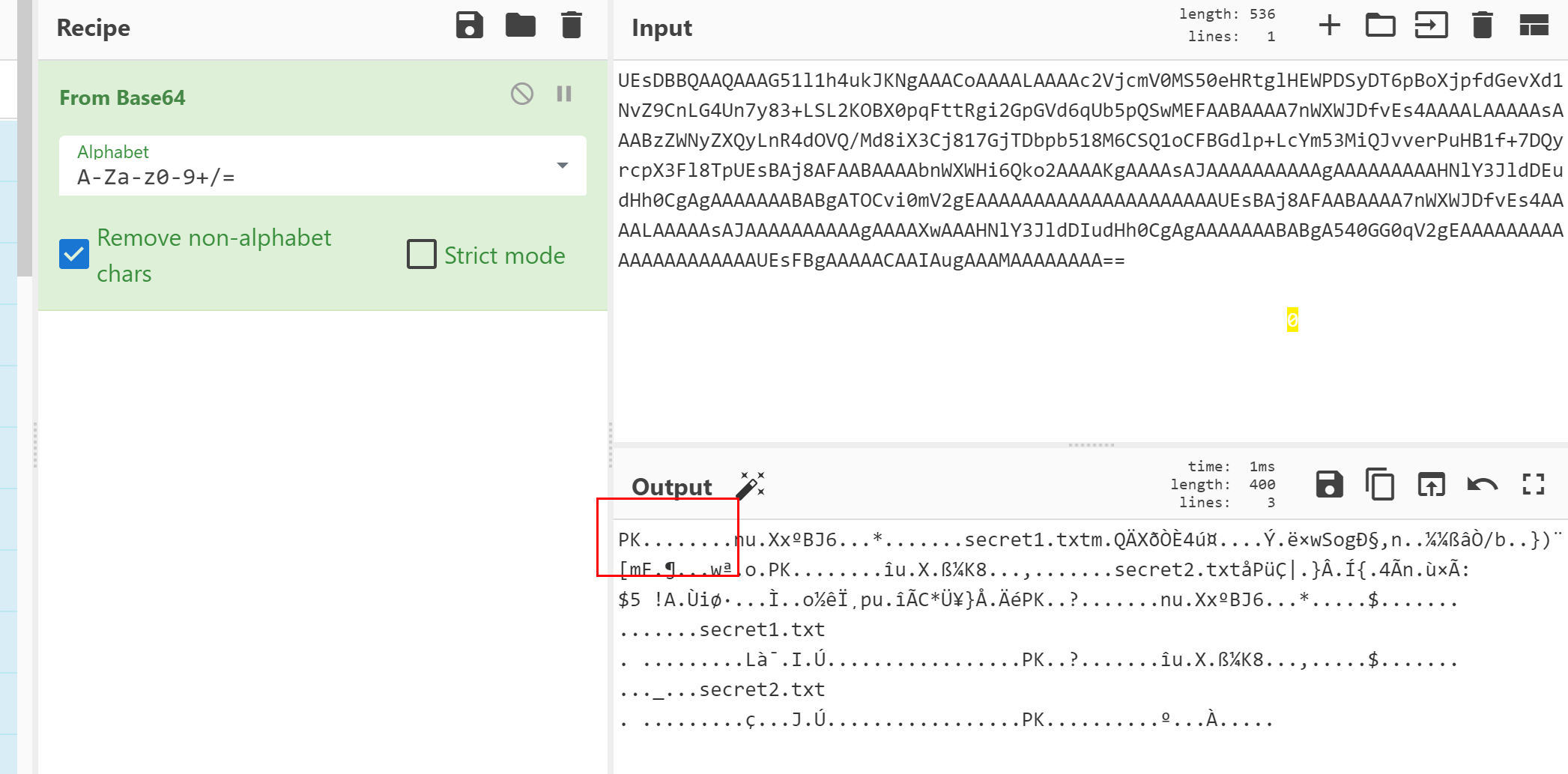 对message两次base64解码后
明显是个zip数据 转出数据得到zip
对message两次base64解码后
明显是个zip数据 转出数据得到zip
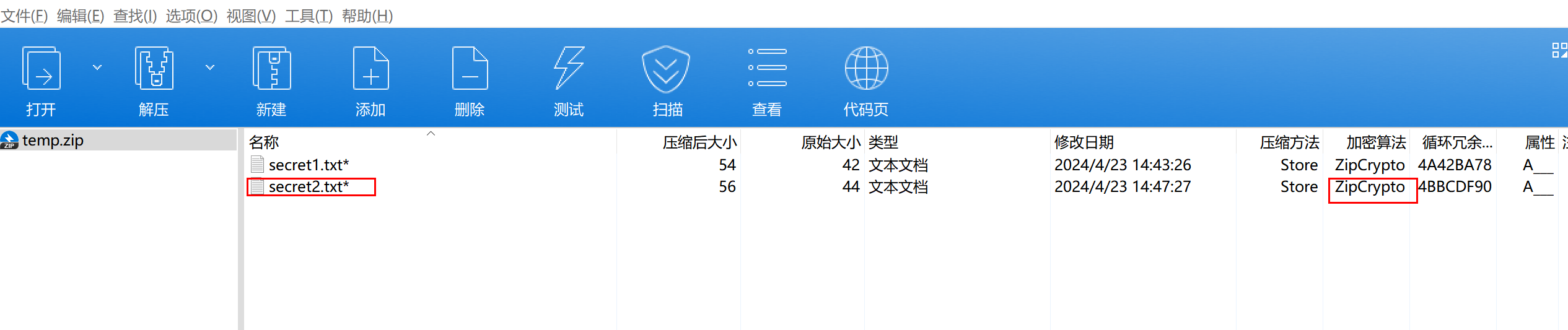 存在
存在secret2.txt同名文件 而且加密算法是ZipCrypto考虑部分明文攻击
创建 secret2.txt 内容为 Hello, but what you're looking for isn't me.
bkcrack.exe -L temp.zip
比对 CRC 是否相同 检验是否可以攻击成功
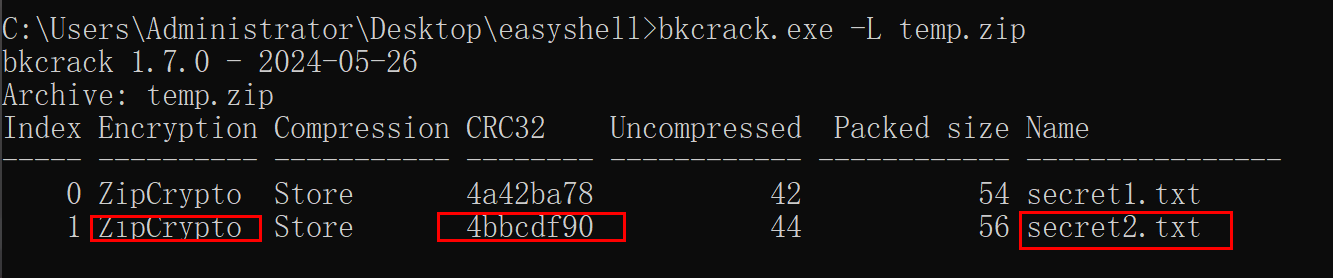
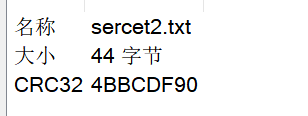 CRC32相同 一定是部分明文攻击
CRC32相同 一定是部分明文攻击
bkcrack -C temp.zip -c secret2.txt -p secret2.txt
攻击成功 可以拿到 key e0c271a4 cbd76d08 8d707128
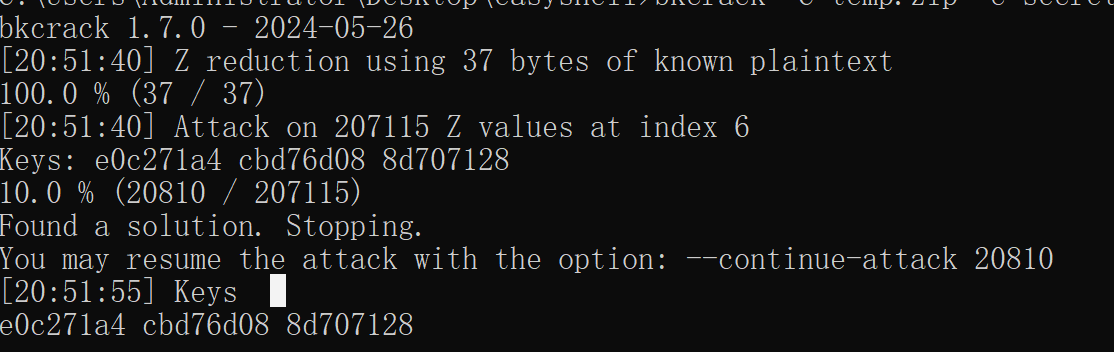
bkcrack -C temp.zip -k e0c271a4 cbd76d08 8d707128 -U flag.zip flag
重新将数据写入新zip 中 压缩密码是 flag
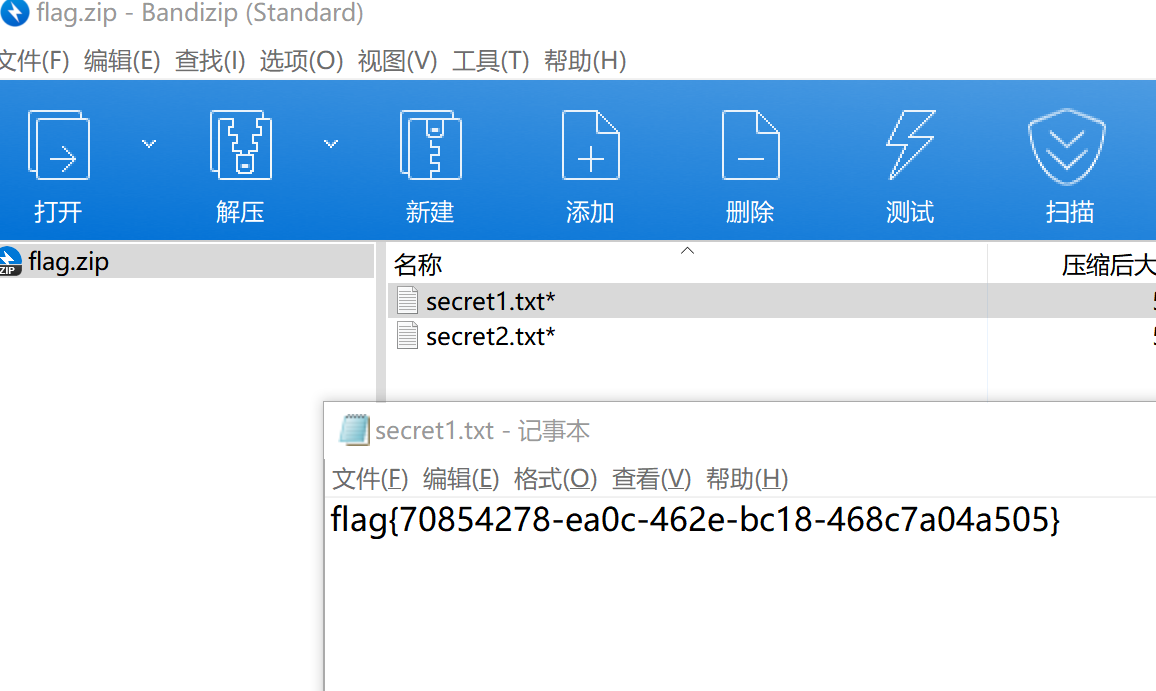 打开就是flag
flag{70854278-ea0c-462e-bc18-468c7a04a505}
打开就是flag
flag{70854278-ea0c-462e-bc18-468c7a04a505}